- Tracking and Analyzing Remote Desktop Activity Logs in Windows
- Error message when you try to log on to a Windows Server 2003-based terminal server: Windows cannot load the user’s profile but has logged you on with the default profile for the system
- Symptoms
- Cause
- Resolution
- More information
- Did this fix the problem
- Как в логах Windows Terminal Server отслеживать внешние IP?
- Windows Terminal Server Log Monitoring
- Track what remote users do on your Windows Terminal Server in Real-Time!
- Windows Terminal Server Log Monitoring using EventLog Analyzer
- EventLog Analyzer’s Windows Terminal Server Log Monitoring Benefits
- Start monitoring Windows Terminal Server activities right away.
- Thanks!
Tracking and Analyzing Remote Desktop Activity Logs in Windows
In this article we’ll consider the features of auditing and analyzing RDP connection logs in Windows. As a rule, the described methods may be useful when investigating RDP-related activity on RDS (terminal) Windows servers in forensics tasks, when a system administrator must provide the information about what users logged on to the RDS server, when a specific RDP user authenticated and ended up the session, which device (a name or IP address) an user connected from. I think this information will be useful both for the administrators of corporate RDS farms and for owners of a separate RDP servers what are published in the Internet (Windows VPS are still quite popular).
You can check the RDP connection logs using Windows Event Viewer ( eventvwr.msc ). Windows logs contain a lot of data, and it is quite difficult to find the event you need. When a user remotely connects to the remote desktop of RDS (RDP), a whole number of events appears in the Windows Event Viewer. There are several different logs where you can find the information about Remote Desktop connections. We’ll look at the logs and events on the main stages of an RDP connection that may be of interest to the administrator:
- Network Connection;
- Authentication;
- Logon;
- Session Disconnect/Reconnect;
- Logoff.
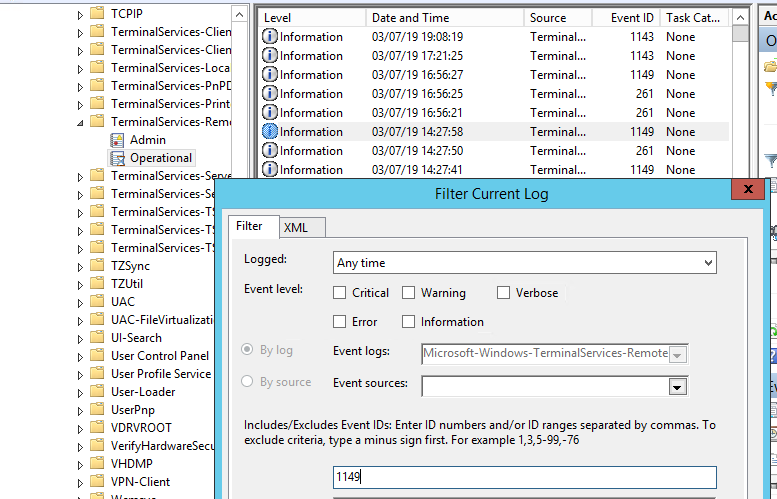
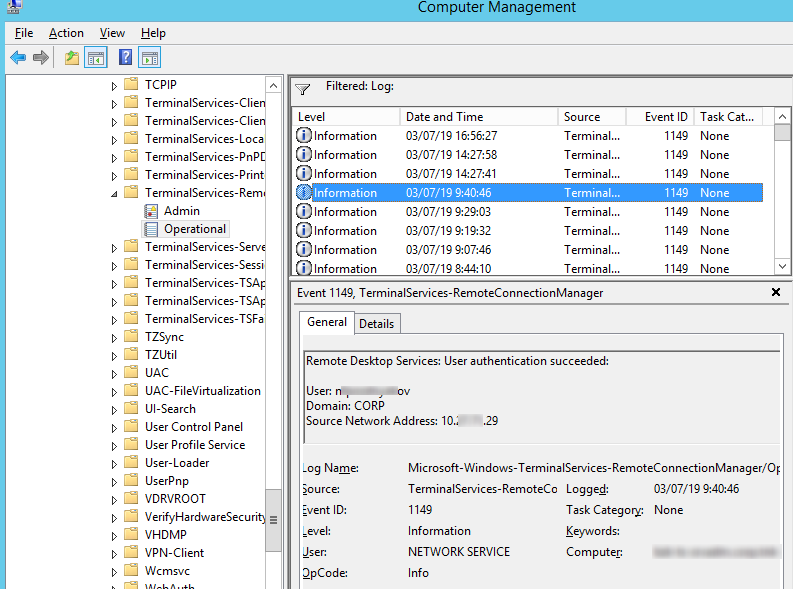
Network Connection is the establishment of a network connection to a server from a user RDP client. It is the event with the EventID 1149 ( Remote Desktop Services: User authentication succeeded ). If this event is found, it doesn’t mean that user authentication has been successful. This log is located in “Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational”. Enable the log filter for this event (right-click the log -> Filter Current Log -> EventId 1149).
Then you will get an event list with the history of all RDP connections to this server. As you can see, the logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event text looks differently) and the IP address of the computer, from which the RDP connection has been initiated.
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located in “Windows -> Security”. So you may be interested in the events with the EventID 4624 ( An account was successfully logged on ) or 4625 ( An account failed to log on ). Please, pay attention to the LogonType value in the event description. If the Remote Desktop service has been use to create new session during log on, LogonType = 10. If the LogonType = 7, it means that a user has reconnected to the existing RDP session.
At the same time, you can find a user name in the event description in the Account Name field, a computer name – in Workstation Name, and an IP address – in Source Network Address.
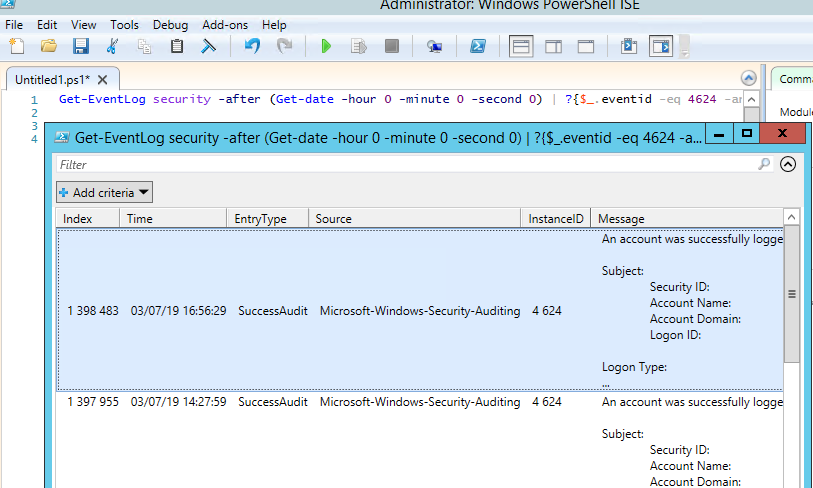
You can get the list of events related to successful RDP authentication (EventID 4624) using this PowerShell command:
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ? <$_.eventid -eq 4624 -and $_.Message -match 'logon type:\s+(10)\s'>| Out-GridView
Logon refers to an RDP logon to the system, an event that appears after a user has been successfully authenticated. It is an event with the EventID 21 ( Remote Desktop Services: Session logon succeeded ). This events are located in the “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. As you can see, here you can find the ID of a user RDP session — Session ID.
The event with the EventID – 21 ( Remote Desktop Services: Shell start notification received ) means that the Explorer shell has been successfully started (the desktop appears in the user’s RDP session).
Session Disconnect/Reconnect – session disconnection / reconnection events have different IDs depending on what caused user disconnection (disconnection to inactivity, Disconnect option has been selected by the user in the session, RDP session ended by another user or an administrator, etc.). You can find these events in the logs located in “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. Let’s consider the most interesting RDP events:
The event with the EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
The event with the EventID 4799 in “Windows -> Security” log ( A session was disconnected from a Window Station ). A user has been disconnected from an RDP session.
Logoff refers to the user logoff from the system. It is logged as the event with the EventID 23 ( Remote Desktop Services: Session logoff succeeded ) in “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”.
At the same time the event with the EventID 4634 ( An account was logged off ) appears in the Security log.
The event with the EventID 9009 ( The Desktop Window Manager has exited with code ) in the System log means that a user has initiated logoff from the RDP session with both the window and the graphic shell of the user have been terminated.
Here is a short PowerShell script that lists the history of all RDP connections for the current day from the terminal RDS server logs. The resulting table shows the connection time, the client’s IP address and the remote user name (if necessary, you can include other LogonTypes to the report).
Sometimes it can be more convenient to view and investigate RDP logs in the Excel table, so you can export any Windows events into a text file and import it in Excel. You can export the log from the Event Viewer GUI (only if the event logs are not cleared), from the command prompt:
WEVTUtil query-events Security > c:\ps\rdp_security_log.txt
get-winevent -logname «Microsoft-Windows-TerminalServices-LocalSessionManager/Operational» | Export-Csv c:\ps\rdp_connection_log.txt -Encoding UTF8
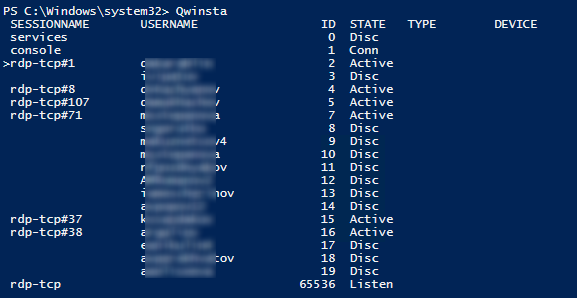
You can display the list of current remote sessions on your RDS server using this command:
The command returns the session ID (ID), the name of user (USERNAME) and the session state (Active/Disconnect). It is convenient to use this command when you need to get the ID of the user RDP session in case shadow connection is used.
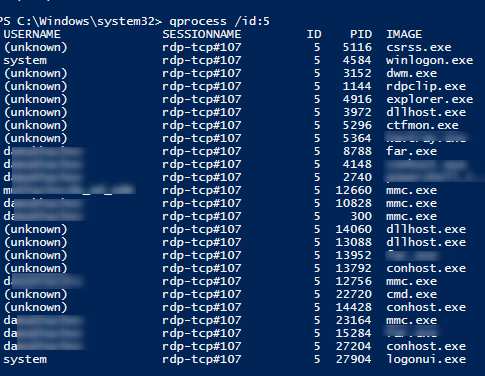
You can display the list of the running processes in the specific RDP session (the session ID is specified):
Logs on an RDP client side are not quite informative, but you can check the history of RDP connections in the user’s registry.
Error message when you try to log on to a Windows Server 2003-based terminal server: Windows cannot load the user’s profile but has logged you on with the default profile for the system
This article provides a solution to an issue that occurs when you log on to a Windows Server 2003-based terminal server.
Original product version: В Windows Server 2003
Original KB number: В 935649
Symptoms
When you try to log on to a Microsoft Windows Server 2003-based terminal server, you receive the following error message:
Windows cannot load the user’s profile but has logged you on with the default profile for the system.
Detail: Insufficient system resources exist to complete the requested service.
When this problem occurs, the following events are logged in the Application log on the terminal server.
Cause
You experience this problem if many users are logged on to the terminal server.
Resolution
This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in Windows
To resolve this problem, modify the registry to increase the PoolUsageMaximum value and the PagedPoolSize value. To do this, follow these steps:
Click Start, click Run, type regedit, and then click OK.
Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
On the Edit menu, point to New, and then click DWORD Value.
In the New Value #1 box, type PoolUsageMaximum, and then press ENTER.
Right-click PoolUsageMaximum, and then click Modify.
In the Value data box, type 60, click Decimal, and then click OK.
If the PagedPoolSize registry entry exists, go to step 8. If the PagedPoolSize registry entry does not exist, create it. To do this, follow these steps:
- On the Edit menu, point to New, and then click DWORD Value.
- In the New Value #1 box, type PagedPoolSize, and then press ENTER.
Right-click PagedPoolSize, and then click Modify.
In the Value data box, type ffffffff, and then click OK.
Exit Registry Editor, and then restart the computer.
More information
For more information, click the following article number to view the article in the Microsoft Knowledge Base:
312362 Server is unable to allocate memory from the system paged pool
Did this fix the problem
Check whether the problem is fixed. If the problem is fixed, you are finished with this section. If the problem is not fixed, you can contact support.
Как в логах Windows Terminal Server отслеживать внешние IP?
Вопрос простой.
Сервер стоит за роутером с NAT и в журнале для всех сессий RDP пишет адрес роутера, а нужно внешние IP адреса отслеживать, чтобы понимать, какой пользователь с каких адресов заходит.
На роутере сложно сделать мониторинг, т.к. там не будет имен пользователей.
Сервер — Windows Server 2016
Роутер — FortiGate 30E
- Вопрос задан более года назад
- 200 просмотров
Juhani Lahtinen, да смотрел, там вообще не найти. Записей 4624 в Security log с логинами нормальными вообще нет. Только анонимные, вроде таких:
Есть 4776, там Credential validation c нормальными логинами, но IP нет, только имена рабочих станций.
«An account was successfully logged on.
Subject:
Security ID: NULL SID
Account Name: —
Account Domain: —
Logon ID: 0x0
Logon Information:
Logon Type: 3
Restricted Admin Mode: —
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: ANONYMOUS LOGON
Account Name: ANONYMOUS LOGON
Account Domain: NT AUTHORITY
Logon ID: 0x1161D9F94
Linked Logon ID: 0x0
Network Account Name: —
Network Account Domain: —
Logon GUID:
Process Information:
Process ID: 0x0
Process Name: —
Network Information:
Workstation Name: SERVER
Source Network Address: fe80::8045:b9f8:7359:8dde
Source Port: 57208
«
Juhani Lahtinen, Ну запрос выдает записи, я их в журнале вижу. Только там не могу найти логины обычных пользователей, только анонимные запросы какие-то внутренние. Тоже с ними надо разбираться, похоже какие-то мак устройства. Выше привел пример.
И адрес вот в таком формате еще выдает Source Network Address: fe80::8045:b9f8:7359:8dde
PS C:\Users\Administrator> Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ? <(4624) -conta
ins $_.EventID -and $_.Message -match ‘Logon type:\s+(3)\s’>
Index Time EntryType Source InstanceID Message
—— —- ——— —— ———- ——-
45855524 янв 27 16:02 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855481 янв 27 16:02 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855429 янв 27 16:01 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855382 янв 27 16:01 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855338 янв 27 16:00 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855291 янв 27 16:00 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855248 янв 27 15:59 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855207 янв 27 15:59 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855165 янв 27 15:58 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855124 янв 27 15:58 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
45855085 янв 27 15:57 SuccessA. Microsoft-Windows. 4624 An account was successfully logged on.
Windows Terminal Server Log Monitoring
Track what remote users do on your Windows Terminal Server in Real-Time!
Organizations allow their employees to work from home and while on business trips by providing them remote connection to access the network. IT security professionals need to securely track the activity of such users by monitoring the terminal server logs in real-time to avoid threats.
With terminal server log monitoring in place, IT security professionals never lose control over remote users and the resources they access. Every action gets captured in the log data generated by the terminal server. If this log data is analyzed, it can give vital security insights to secure your network from potential threats.
Most importantly organizations can achieve the stringent compliance requirements set by various regulatory bodies for preventing security breaches.
Windows Terminal Server Log Monitoring using EventLog Analyzer
EventLog Analyzer allows you to monitor and generate reports on user activities that happen on your Windows remote desktop services by monitoring and analyzing the terminal server log data in real-time. It analyzes the time spent by users in every remote connection session, which users are logged on to the server, which resource was accessed, was authorization granted to the users, whether the user successfully connected to the resource, and more.
EventLog Analyzer’s Windows Terminal Server Log Monitoring Benefits
- Centralized Terminal Server Log Monitoring – Get precise information about resources, user activities, and users connected, all in one central place
- Track user activities – Get detailed information on user activities and the resources accessed by them. Know who is logging on to your servers and the total time they remain connected
- Meet regulatory compliance requirements – Monitoring user activities over remote connections help in meeting regulatory compliance requirements by securing your network from breaches and threats
- Number of Authorized Terminal Sessions — Know the total number of terminal sessions that were authorized in a given time frame
Start monitoring Windows Terminal Server activities right away.
Thanks!
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here