- Windows Threats Removing
- Windows Threats Removing Description
- What Does a Windows Threats Removing Infection Looks Like, and What Windows Threats Removing Really Is
- History of Windows Threats Removing and the Fake Microsoft Security Essentials Alert Malware Family
- Technical Information
- Screenshots & Other Imagery
- File System Details
- Site Disclaimer
- Leave a Reply
- Your comment is awaiting moderation.
- Please verify that you are not a robot.
- Средство проверки безопасности (Майкрософт) Microsoft Safety Scanner
- Важная информация Important information
- Требования к системе System requirements
- Запуск проверки How to run a scan
Windows Threats Removing
Windows Threats Removing Description
What Does a Windows Threats Removing Infection Looks Like, and What Windows Threats Removing Really Is
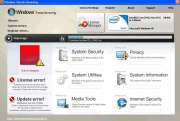
Windows Threats Removing is part of the ever-growing Fake Microsoft Security Essentials Alert Malware family. So, a Windows Threats Removing infection begins with the same old fake alerts used by all the other malware in this group. The fake alert malware, which is a Trojan, is hidden in a fake online virus scanner, malicious link, or freeware download. The Trojan downloads quietly and secretly, and once it is on your computer, it begins to generate alerts that look as if they are being generated by Microsoft Security Essentials. The alerts will pop-up from the System Tray, and they will warn that a Trojan has been found on the system. The alerts will recommend a scan, and if you agree to the scan, you will see another alert that says that the threat has been identified as a specific Trojan. This same alert will also recommend a download of anti-virus software in order to remove the «threat,» and if you agree to download it, you are agreeing to download Windows Threats Removing in order to remove a threat that isn’t actually there.
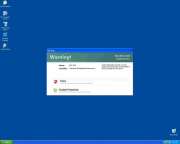
Windows Threats Removing causes a very standard set of symptoms. When you turn on your computer, as Windows starts, you will see the bogus Windows Threats Removing home screen before you see the desktop. This home screen uses the Windows name and logo, without permission, in order to trick you into thinking that Windows Threats Removing is somehow legitimate software. The only way to get past the Windows Threats Removing home screen is to let Windows Threats Removing run one of its fake system scans, which is something that Windows Threats Removing will do every time Windows starts. These fake scans will always turn up lists of fake results, after which Windows Threats Removing will always tell you that if you want to remove these numerous «threats,» you need to purchase a license for Windows Threats Removing. If you follow that recommendation, you can give your credit card number to the crooks behind Windows Threats Removing, who will charge it and give you nothing in return. Windows Threats Removing is incapable of being useful or becoming useful, regardless of whether or not you pay for Windows Threats Removing.
Once you’ve cleared the phony Windows Threats Removing home screen, your computer will not be any more usable than it was while you were waiting through that fake scan. Windows Threats Removing will prevent other programs from running, including Task Manager, so you can’t use Task Manager to stopl Windows Threats Removing. If you try to go online for help, Windows Threats Removing can redirect you to its own websites, or prevent you from accessing the Internet at all. Meanwhile, Windows Threats Removing will create a constant stream of fake alerts and error messages, which will continually repeat a handful of weird warnings about your ordinary programs and Windows services being somehow malicious. Of course, these warning messages will prompt you to purchase a license for Windows Threats Removing. Keep in mind that paying for a license – paying the ransom – will not cause Windows Threats Removing to leave you alone.
History of Windows Threats Removing and the Fake Microsoft Security Essentials Alert Malware Family
The family of fake security programs that Windows Threats Removing comes from is one that has been causing infections, under various names, for the past several months. Really, there’s just one piece of malware, and every day it is re-released under a new name. Regardless of what it is called, this malware is part of a widespread Russian scam. In addition to using proper anti-virus software, you can avoid another infection with one of Windows Threats Removing’s relatives by watching out for anything that calls itself security software and names itself according to the table below. «Windows» is always the first word, and the second and third words are chosen from the lists. The second or third word may be eliminated, creating a two-word name, such as «Windows Remedy.» Keep your eyes peeled!
Technical Information
Screenshots & Other Imagery

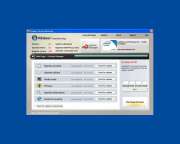
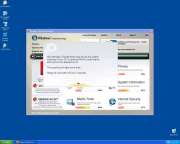
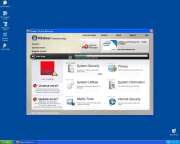
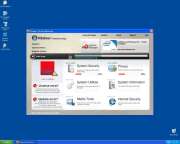

File System Details
| # | File Name | Size | MD5 | Detection Count |
|---|---|---|---|---|
| 1 | %AppData%\Microsoft\fmajil.exe | 2,688,512 | cc4f6944994baacd82c7f94e0f195550 | 1 |
Site Disclaimer
Enigmasoftware.com is not associated, affiliated, sponsored or owned by the malware creators or distributors mentioned on this article. This article should NOT be mistaken or confused in being associated in any way with the promotion or endorsement of malware. Our intent is to provide information that will educate computer users on how to detect, and ultimately remove, malware from their computer with the help of SpyHunter and/or manual removal instructions provided on this article.
This article is provided «as is» and to be used for educational information purposes only. By following any instructions on this article, you agree to be bound by the disclaimer. We make no guarantees that this article will help you completely remove the malware threats on your computer. Spyware changes regularly; therefore, it is difficult to fully clean an infected machine through manual means.
Leave a Reply
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our «Billing Questions or Problems?» page. For general inquiries (complaints, legal, press, marketing, copyright), visit our «Inquiries and Feedback» page.
Your comment is awaiting moderation.
Please verify that you are not a robot.
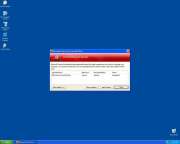
The ESL Threat Scorecard is an assessment report that is given to every malware threat that has been collected and analyzed through our Malware Research Center. The ESL Threat Scorecard evaluates and ranks each threat by using several metrics such as trends, incidents and severity over time.
In addition to the effective scoring for each threat, we are able to interpret anonymous geographic data to list the top three countries infected with a particular threat. The data used for the ESL Threat Scorecard is updated daily and displayed based on trends for a 30-day period. The ESL Threat Scorecard is a useful tool for a wide array of computer users from end users seeking a solution to remove a particular threat or security experts pursuing analysis and research data on emerging threats.
Each of the fields listed on the ESL Threat Scorecard, containing a specific value, are as follows:
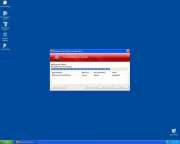
Ranking: The current ranking of a particular threat among all the other threats found on our malware research database.
Threat Level: The level of threat a particular computer threat could have on an infected computer. The threat level is based on a particular threat’s behavior and other risk factors. We rate the threat level as low, medium or high. The different threat levels are discussed in the SpyHunter Risk Assessment Model.
Infected Computer: The number of confirmed and suspected cases of a particular threat detected on infected computers retrieved from diagnostic and scan log reports generated by SpyHunter’s Spyware Scanner.
% Change: The daily percent change in the frequency of infected computers of a specific threat. The formula for percent changes results from current trends of a specific threat. An increase in the rankings of a specific threat yields a recalculation of the percentage of its recent gain. When a specific threat’s ranking decreases, the percentage rate reflects its recent decline. For a specific threat remaining unchanged, the percent change remains in its current state. The % Change data is calculated and displayed in three different date ranges, in the last 24 hours, 7 days and 30 days. Next to the percentage change is the trend movement a specific malware threat does, either upward or downward, in the rankings. Each level of movement is color coded: a green up-arrow (∧) indicates a rise, a red down-arrow (в€Ё) indicates a decline, and a brown equal symbol (=) indicates no change or plateaued.
Top 3 Countries Infected: Lists the top three countries a particular threat has targeted the most over the past month. This data allows computer users to track the geographic distribution of a particular threat throughout the world.
Средство проверки безопасности (Майкрософт) Microsoft Safety Scanner
Средство проверки безопасности (Майкрософт) — это инструмент, дающий возможность проверять компьютеры с Windows на наличие вредоносных программ и удалять обнаруженные вредоносные программы. Microsoft Safety Scanner is a scan tool designed to find and remove malware from Windows computers. Просто скачайте это средство и запустите проверку, чтобы обнаружить вредоносные программы и попытаться вернуть систему в рабочее состояние, устранив изменения, сделанные выявленными вредоносными компонентами. Simply download it and run a scan to find malware and try to reverse changes made by identified threats.
С ноября 2019 года средство проверки безопасности будет использовать только подпись SHA-2. Starting November 2019, Safety Scanner will be SHA-2 signed exclusively. Для запуска средства проверки безопасности необходимо обновить устройства для поддержки SHA-2. Your devices must be updated to support SHA-2 in order to run Safety Scanner. Дополнительные сведения см. в статье Требование поддержки подписи кода SHA-2 в 2019 г. для Windows и WSUS. To learn more, see 2019 SHA-2 Code Signing Support requirement for Windows and WSUS.
Важная информация Important information
Версия обновления механизма обнаружения угроз в средстве проверки безопасности (Майкрософт) совпадает с версией, описанной на этой веб-странице. The security intelligence update version of the Microsoft Safety Scanner matches the version described in this web page.
Средство проверки безопасности выполняет проверку только при запуске в ручную. Использовать средство проверки безопасности можно только в течение 10 дней после скачивания. Safety Scanner only scans when manually triggered and is available for use 10 days after being downloaded. Рекомендуем скачивать последнюю версию этого средства перед каждой проверкой. We recommend that you always download the latest version of this tool before each scan.
Средство проверки безопасности — это переносимое исполняемое приложение, для него не создается элемент в меню «Пуск» в Windows и значок на рабочем столе. Safety scanner is a portable executable and does not appear in the Windows Start menu or as an icon on the desktop. Запомните, в какую папку вы скачали его. Note where you saved this download.
Это средство не заменяет используемый вами продукт для защиты от вредоносных программ. This tool does not replace your antimalware product. Для защиты в режиме реального времени с функцией автоматического обновления используйте антивирусную программу в Microsoft Defender в Windows 10 и Windows 8 или Microsoft Security Essentials в Windows 7. For real-time protection with automatic updates, use Microsoft Defender Antivirus on Windows 10 and Windows 8 or Microsoft Security Essentials on Windows 7. Эти решения для защиты от вредоносных программ также обладают мощными возможностями по удалению вредоносных программ. These antimalware products also provide powerful malware removal capabilities. Если у вас возникают сложности с удалением вредоносных программ при использовании этих продуктов, ознакомьтесь со справкой в разделе Удаление сложных угроз. If you are having difficulties removing malware with these products, you can refer to our help on removing difficult threats.
Требования к системе System requirements
Средство проверки безопасности помогает удалять вредоносные программы с компьютеров под управлением операционных систем Windows 10, Windows 10 Tech Preview, Windows 8.1, Windows 8, Windows 7, Windows Server 2019, Windows Server 2016, Windows Server Tech Preview, Windows Server 2012 R2, Windows Server 2012, Windows Server 2008 R2 и Windows Server 2008. Safety Scanner helps remove malicious software from computers running Windows 10, Windows 10 Tech Preview, Windows 8.1, Windows 8, Windows 7, Windows Server 2019, Windows Server 2016, Windows Server Tech Preview, Windows Server 2012 R2, Windows Server 2012, Windows Server 2008 R2, or Windows Server 2008. См. политику жизненного цикла Майкрософт. Please refer to the Microsoft Lifecycle Policy.
Запуск проверки How to run a scan
- Скачайте это средство и откройте его. Download this tool and open it.
- Выберите нужный тип проверки и запустите проверку. Select the type of scan that you want to run and start the scan.
- Просмотрите результаты проверки, показанные на экране. Review the scan results displayed on screen. Подробные результаты обнаружения находятся в файле %SYSTEMROOT%\debug\msert.log. For detailed detection results, view the log at %SYSTEMROOT%\debug\msert.log.
Чтобы удалить это средство, удалите его исполняемый файл (по умолчанию это msert.exe). To remove this tool, delete the executable file (msert.exe by default).
Дополнительные сведения о средстве проверки безопасности см. в статье Устранение неполадок с помощью средства проверки безопасности. For more information about the Safety Scanner, see the support article on how to troubleshoot problems using Safety Scanner.